Our graduate student, Mr. Ono, and Prof. Sato gave research presentations in IEEE International Symposium on Circuits and Systems 2021 held in Hybrid (Online + On-site (Daegu, Korea)) from May 23 to 26, 2021 (Presentation date: 25th for Sato and 27th for Ono).
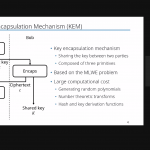
Ono’s presentation is about automatic parameter tuning for GPU implementation of module learning with errors (MLWE) problem-based quantum key exchange. Post-quantum cryptography, which is resilient against attacks using quantum computers, has been attracting attention, and Kyber is one of the examples.
Since the MLWE problem involves a matrix manipulations with polynomial elements, GPU-based implementations have been proposed because of their capability for highly parallel data processing. However, since performance requirements, such as latency and throughput, vary from application to application, and since there exist a broad range of GPUs, it is necessary to optimize the implementation for each application. In this study, we proposed a GPU implementation of Kyber that allows the user to configure the parameters, and an auto-tuning framework that measures the performance and determines the optimal parameters. The evaluation function used to determine the parameters can be defined by the user, allowing optimization according to requirements. The proposed framework improves the performance by up to 85.5% compared to the original implementation when the evaluation function is the latency-to-throughput ratio. We have made our implementation available as open source.
Sato’s presentation is on Clonable PUFs (CPUFs), which are physically unclonable function (PUF) circuits that allow for cloning during fabrication time only. PUFs are emerging as a security primitive, but have an issue that the authentication protocol is centralized on the server that owns the challenge-response pair database. In this paper, we proposed a new concept of PUF that allows for a decentralized authentication among individual PUFs, as opposed to the existing centralized authentication scheme.